DNS SERVER
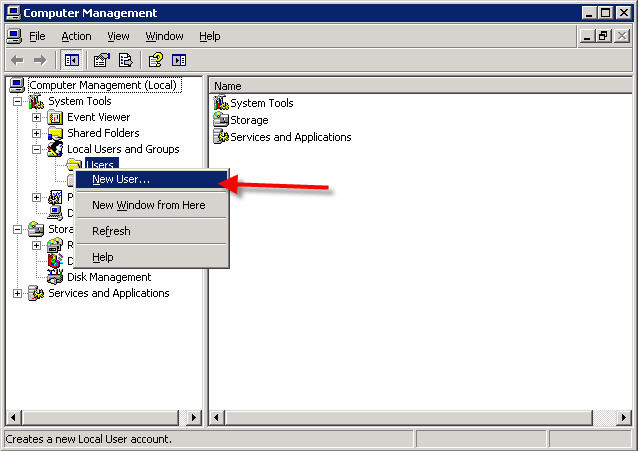
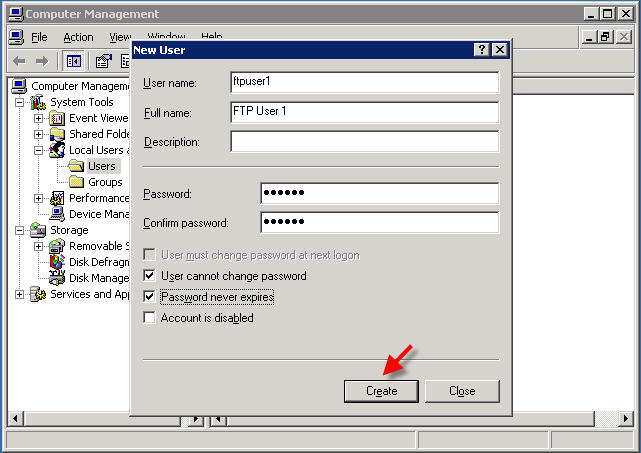
1) How to install DNS server:
Domain Name System (or Service or
Server), an Internet service that translates domain names into IP
addresses. Because domain names are alphabetic, they're easier to
remember. The Internet however, is really based on IP addresses.
Every time you use a domain name, therefore, a DNS service must
translate the name into the corresponding IP address.
Linux DNS (BIND) Configuration
Hostname:dns
Domain name:example.com
Full domain Name:dns.examle.com
Red line show the
changes of the file
Make sure system ip has been static
If
not make a static
[root@dns ~]# system-config-network
[root@dns ~]# service network restart
Step- 1: On Dns Server
install bind and caching server RPM Packages using yum or rpm
[root@dns ~]# yum install bind*
caching-nameserver*
Check server installed
[root@dns ~]# rpm -qa | grep bind*
ypbind-1.19-7.el5
bind-utils-9.3.3-7.el5
bind-9.3.3-7.el5
bind-libbind-devel-9.3.3-7.el5
bind-libs-9.3.3-7.el5
bind-sdb-9.3.3-7.el5
bind-devel-9.3.3-7.el5
binutils-2.17.50.0.6-2.el5
bind-chroot-9.3.3-7.el5
[root@dns ~]# rpm -qa | grep
caching-nameserver
caching-nameserver-9.3.3-7.el5
Step 2:- Go to
/var/named/chroot/etc/ Directory
[root@dns ~]# cd
/var/named/chroot/etc/
[root@dns etc]# pwd
/var/named/chroot/etc
[root@dns etc]# ll -lrt
total 48
-rw-r----- 1 root named 1100 Jan 17
2007 named.caching-nameserver.conf
-rw-r--r-- 1 root root 109 Apr 18
20:55 localtime
-rw-r--r-- 1 root named 113 Apr 18
21:20 rndc.key
-rw-r----- 1 root named 954 Apr 18
21:47 named.rfc1912.zone
Step 3:- copy
named.caching-nameserver.conf to named.conf
[root@dns etc]# cp
named.caching-nameserver.conf named.conf
Step 4:- Edit named.conf file
[root@dns ~]# vi named.conf
//
// named.caching-nameserver.conf
//
// Provided by Red Hat
caching-nameserver package to configure the
// ISC BIND named(8) DNS server as a
caching only nameserver
// (as a localhost DNS resolver only).
//
// See /usr/share/doc/bind*/sample/ for
example named configuration files.
//
// DO NOT EDIT THIS FILE - use
system-config-bind or an editor
// to create named.conf - edits to this
file will be lost on
// caching-nameserver package upgrade.
//
options {
listen-on
port 53 { 192.168.1.2; }; ( CHANGE YOUR DOMAIN SERVER IP)
# listen-on-v6 port 53 { ::1;
};(COMMENT ON THAT LINE)
directory "/var/named";
dump-file
"/var/named/data/cache_dump.db";
statistics-file
"/var/named/data/named_stats.txt";
memstatistics-file
"/var/named/data/named_mem_stats.txt";
query-source port 53;
query-source-v6 port 53;
allow-query
{ any; }; (MAKE A ANY)
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
view localhost_resolver {
match-clients { any; };
(MAKE A ANY)
match-destinations
{ 192.168.1.2; }; (CHANGE YOUR DOMAIN SERVER IP)
recursion yes;
include
"/etc/named.rfc1912.zones";
SAVE AND QUITE THE named.conf
Step 5:- Change ownership of
named.conf
[root@dns etc]# chown root:named
named.conf
[root@dns etc]# ll named.conf
-rw-r----- 1 root named 1093 Apr 18
21:31 named.conf
Step 6:- Edit named.rfc1912.zones for
Zone
[root@dns etc]# vi named.rfc1912.zones
// named.rfc1912.zones:
//
// Provided by Red Hat
caching-nameserver package
//
// ISC BIND named zone configuration
for zones recommended by
// RFC 1912 section 4.1 : localhost
TLDs and address zones
//
// See /usr/share/doc/bind*/sample/ for
example named configuration files.
//
zone "." IN {
type hint;
file "named.ca";
};
zone "example.com"
IN { (CHANGE YOUR DOMAIN NAME)
type master;
file "forword.zone";
(CHANGE YOUR FORWORD ZONE FILE NAME)
allow-update { none; };
};
zone "localhost" IN {
type master;
file "localhost.zone";
allow-update { none; };
};
zone "1.168.192.in-addr.arpa"
IN { (REVERSE IP ADDRESS DOMAIN SERVER)
type master;
file "reverse.zone";
(CHANGE YOUR REVERSE ZONE FILE NAME)
allow-update { none; };
};
SAVE AND QUITE the named.rfc1912.zones
Step 7:- Make a simlink named.conf
to /etc folder
[root@dns etc]# ln -s
/var/named/chroot/etc/named.conf /etc/named.conf
Go to /etc folder to check
simlink
[root@dns etc]# ll named.conf
lrwxrwxrwx 1 root root 32 Apr 18
21:29 named.conf -> /var/named/chroot/etc/named.conf
Step 8:- Go to
/var/named/chroot/var/named/ to Make Zone conf file
[root@dns etc]# cd
/var/named/chroot/var/named/
Copy localdomain.zone to
forword.zone
[root@dns named]# cp localdomain.zone
forword.zone
And Copy named.local to reverse.zone
[root@dns named]# cp named.local
reverse.zone
Step 9:-Edit forword.zone
$TTL 86400
@ IN SOA
dns.example.com. root.dns.example.com
(
42 ; serial (d. adams)
3H ; refresh
15M ; retry
1W ; expiry
1D ) ; minimum
IN
NS example.com
dns IN
A 192.168.1.2
That’s red line show the changes
of the file SAVE AND QUITE
Step 10:-Edit reverse.zone file
$TTL 86400
@ IN
SOA example.com. root.dns.example.com. (
1997022700 ; Serial
28800 ; Refresh
14400 ; Retry
3600000 ; Expire
86400 ) ; Minimum
IN NS
dns.example.com.
2 IN PTR
dns.example.com.
That’s red line show the changes
of the file
SAVE AND QUITE the reverse.zone
Step 11:- Change ownership
forword.zone and reverse.zone file
[root@dns named]# chown root:named
forword.zone
[root@dns named]# chown root:named
reverse.zone
Step 12:-Check entry in /etc/hosts
file
[root@dns named]# cat /etc/hosts
# Do not remove the following line, or
various programs
# that require network functionality
will fail.
127.0.0.1 dns.example.com
dns localhost.localdomain localhost
::1 localhost6.localdomain6
localhost6
192.168.1.2 dns.example.com dns
( YOUR DOMAIN NAME AND IP)
Step 13:-Check entry in
/etc/resolve.conf
[root@dns named]# cat /etc/resolv.conf
search
example.com ( YOUR DOMAIN NAME)
nameserver
192.168.1.2 (YOUR DOMAIN IP ADDRESS )
Step 14:- Restart the named service
[root@dns ~]# service named restart
Stopping named:
[FAILED]
Starting named:
[ OK ]
Step 15:- Check the name resolve
[root@dns ~]# dig dns.example.com
; <<>> DiG 9.3.3rc2 <<>>
dns.example.com
;; global options: printcmd
;; Got answer:
;; ->>HEADER<<- opcode:
QUERY, status: NOERROR, id: 29727
;; flags: qr aa rd ra; QUERY:
1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 0
;; QUESTION SECTION:
;dns.example.com. IN A
;; ANSWER SECTION:
dns.example.com. 86400 IN A
192.168.1.2
;; AUTHORITY SECTION:
example.com. 86400 IN
NS example.com.example.com.
;; Query time: 11 msec
;; SERVER: 192.168.1.2#53(192.168.1.2)
;; WHEN: Fri Apr 19 06:45:51 2013
;; MSG SIZE rcvd: 79
AND AFTER CHECK IP TO NAME
[root@dns ~]# dig -x 192.168.1.2
; <<>> DiG 9.3.3rc2 <<>>
-x 192.168.1.2
;; global options: printcmd
;; Got answer:
;; ->>HEADER<<- opcode:
QUERY, status: NOERROR, id: 35101
;; flags: qr aa rd ra; QUERY: 1,
ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1
;; QUESTION SECTION:
;2.1.168.192.in-addr.arpa. IN
PTR
;; ANSWER SECTION:
2.1.168.192.in-addr.arpa. 86400 IN
PTR dns.example.com.
;; AUTHORITY SECTION:
1.168.192.in-addr.arpa. 86400 IN
NS dns.example.com.
;; ADDITIONAL SECTION:
dns.example.com. 86400 IN A
192.168.1.2
;; Query time: 18 msec
;; SERVER: 192.168.1.2#53(192.168.1.2)
;; WHEN: Fri Apr 19 06:44:28 2013
;; MSG SIZE rcvd: 105
------------------------------